In this post I will breakdown a random malware found online.
By opening the file we can see that we are asked to enable the embedded macro.
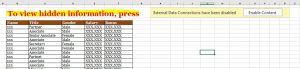
When we examine the macro itself, we notice that the macro is trying to create a powershell script at “%TEMP%\Catchme\1.ps1″ – my pleasure!
The powershell script is encoded within the cells itself, not something clever.
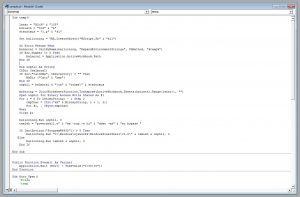
Lets modify the script and remove the last 7 lines from the function temp() so we can get that powershell script without running it.
The script itself contains some encoded and compressed .NET managed code which will be loaded using System.Reflection.Assembly.Load(byte []).
The assembly is loaded into the application domain of the caller.
But we really want to get the executable itself – its way more fun this way!
To debug .NET assemblies we have some wonderful WinDBG extensions called SOS and SOSEX.
First load sosex.dll to WinDBG
.load “C:\\Users\\mark\\Desktop\\don’t open – dead inside\\sosex.dll”
Next step is settings breakpoints. We are interested in “System.Reflection.Assembly.Load”
!mbm *Assembly.Load*
We got our desired function call!
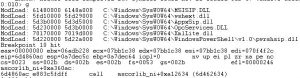
Because our debugger stopped exactly before “System.Reflection.Assembly.Load” is called, we can look at the stack and get the pointer to the file.
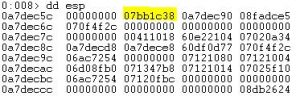
All we have left to do is dump the file and take a look at it
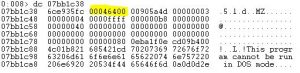
.writemem “C:\\Users\\mark\\Desktop\\don’t open – dead inside\\dumped.dll” 07bb1c40 L00046400
After all that work, all we get is a variant of QuasarRAT.
IOC:
sample.xls – md5,70659C4950B32B57DEA60E81DC64279B
1.ps1 – md5,D88A4430EB40F3C6731D66D6FFCB0724
loaded dll – md5,9581221589F01FE90358D31D3450E9A8