On Israel’s 69th independence day, the Mossad posted a new CTF challenge for us to break.
As always, challenge accepted.

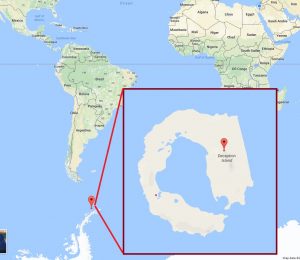
We notice the following URL: http://62933120s,60561450w.xyz and if we check those coordinates (-62.933120,-60.561450) in google maps, we get an island – Deception Island.
Challenge #1
Welcome back Agent C!
Once again we require your skills for an urgent mission.
Our intelligence officers have intercepted a message between notorious terrorists discussing an imminent attack on targets world-wide.
Intel points to a popular chat website used by these terrorists to coordinate and select rendezvous locations.
Your mission is to track the team online and ascertain their physical location.
The following link leads to the web site of the online chat service.
Good luck!,
M.
Our mission is find the terrorists and their location using given chat system. sounds easy?
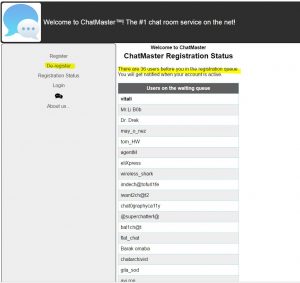
When we register to the chat, we have our first obstacle: there is a queue of 36 people waiting to register, and only the first one will be approved each day.
The bright side, if we give up, we can de-register and remove ourselves from the queue.
We will find a way to de-register the other users.
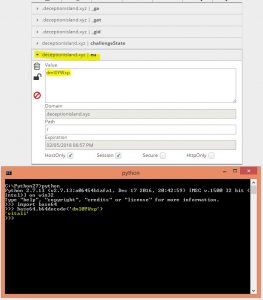
While inspecting the cookies we noticed that the logged user defined by it’s cookie, to be more specific – base64 of the username.
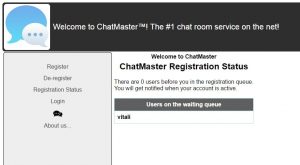
After de-registering all the other users, we end up being the only one in the queue.
At this point we can simply login and start chatting.
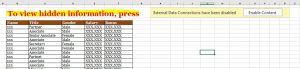
We cannot view the entire room list because this section is closed for premium members.
Sorry, This area is reserved for our PLATINUM members only…
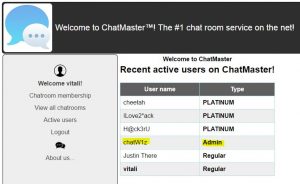
But we can view the active users list.
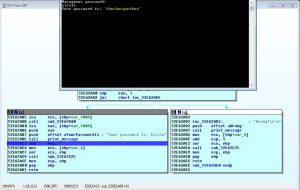
One of the users is an administrator, we will try to reset his password.
The hint we get is a link to a file which will lead us to the password – hopefully.
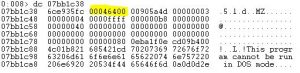
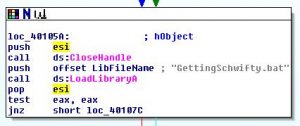
The file named “password_hint” without extension, but by checking file’s magic number (50 4B 03 04) we can see its a zip (might also be jar, docx, xlsx, etc.), which contains a .dll file.
But like all good things in life, its password protected.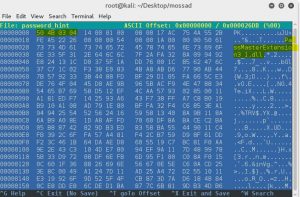
Luckily the password was very easy to brute force.
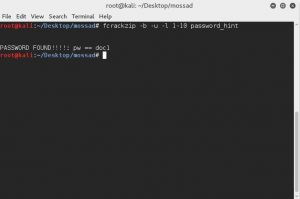
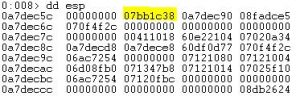
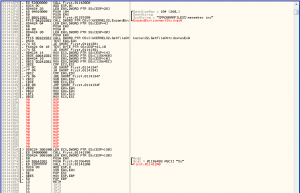
We open the DLL with IDA and set a breakpoint at the relevant location (usually where the prints/validations happening).
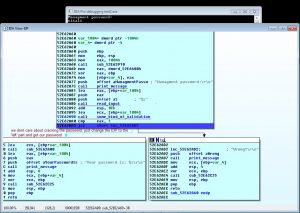
We dont care about asked password, simply jump to the correct section and the program will display the desired password.
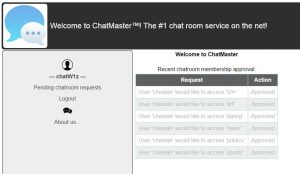
Connecting to admin’s account will let us approve users asking to join a room, I guess we need to join a room (platinum?).
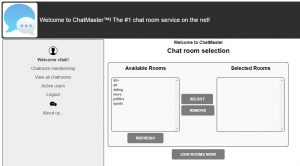
Joining the “regular” rooms did not help us.
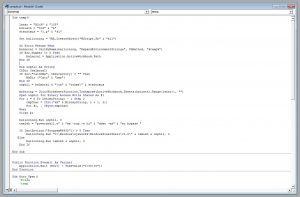
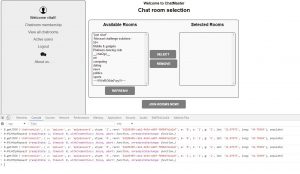
After digging entire website’s source code the only piece of usable code was the javascript at room selection page.
And the source code behind:

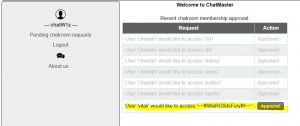
We played with the parameters and found a combination which displayed the entire room list.
You can be only in one room at a time, and the luck was against us – the correct room was the last one.
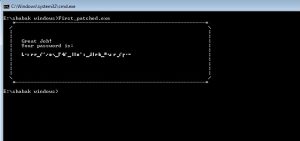
Thanks to chatW1z we got into the room.
And the secret message inside the chat room:
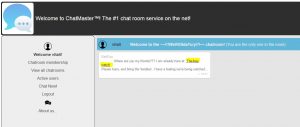
Found you!
Challenge #2
Well done Agent!
The location you recovered was correct and we dispatched our tactical team.
However, the terrorist group was already gone by the time they arrived. We gathered enough intel to determine that the terrorists have planted a bomb on an airplane somewhere in the world, but we do not know the flight number and/or its destination.
We did however recover a picture of the bomb from the terrorist meeting.
Our steganography expert insists that the picture contains a hidden message, but she was unsuccessful in uncovering it before she left on her honeymoon.
We require your assistance in locating and defusing the bomb before it detonates.
There isn’t much time…
Good luck!,
M.
The next challenge begins with an image:
Lucky for us, the stenography wasn’t too hard and zsteg detected it without problems.
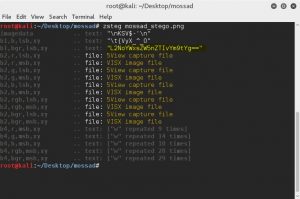
And we got our next target.
Our mission is to defuse the bomb. we have to find that password quickly.
Browsing the site, we found a link to bomb’s firmware, lets hope the password is there.

The downloaded file is a zip, and inside there was the firmware.
Firmware itself was some kind of linux file system (might be bootable?), we dont care, just mount it.
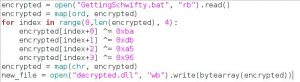
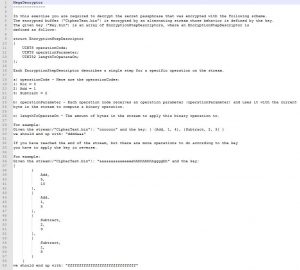
We found the source code of the defuse mechanism, next step is finding the password using ‘Pmgmt.pyc’ file.
We can either brute force our way using the ‘CheckPassword’ function, or reverse the .pyc file and see what is in there.
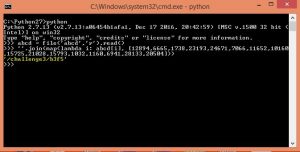
By de-compiling Pmgmt.pyc we notice the ‘GetPassword’ function, which is a simple ‘password_array[index]’ implementation.
The index stored in a different file: ‘/etc/iexprun’, so we copy that file from the mounted folder to our file system, and run the function.
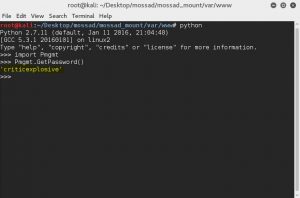
Easy-Peasy!
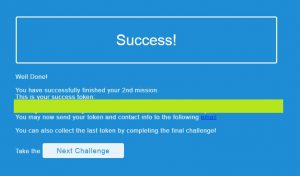
Challenge #3
You did it again!
The bomb you defused was discovered soon after the airplane landed (seems that someone posted an anonymous tip to local authorities…).
Additionally, we have been able to recruit an agent within the terrorist cell.
We are unable to maintain constant contact with him as the agent is deep undercover.
However, he did manage to post a message to our secure servers. We require your skills once again in order to follow the communication trail and reveal the message.
Thanks, and good luck!,
M.
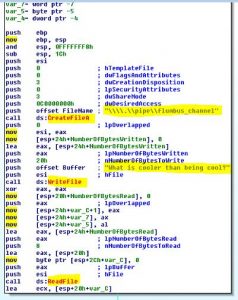
We get a link to a message that we need to get info from.
This message is a PCAP file, so lets open with Wireshark.
Again, life is hard, and the traffic is is encrypted over SSL.
Fortunately we got some clues from ICMP requests.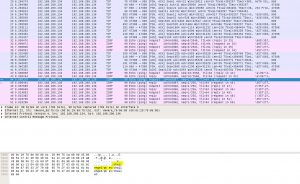
(‘/challenge3/pkey’, ‘/challenge3/abcd’, ‘secret’)
The first file, ‘abcd’, is a copy-paste from Mossad’s page on Wikipedia.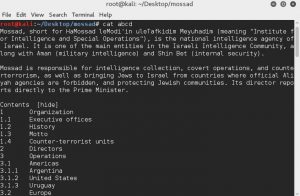
The second file, ‘pkey’, is literately the pkey.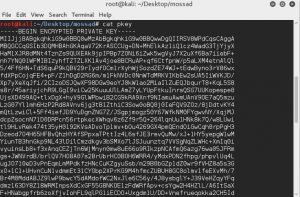
Lets try adding that key to Wireshark and hope the packets will be decrypted.
* The key is not in the supported format, so we have to fix it.
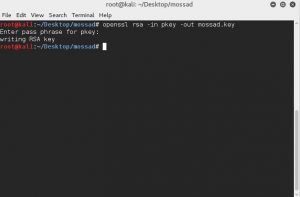
Add the key:
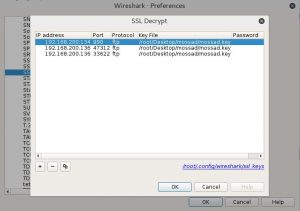
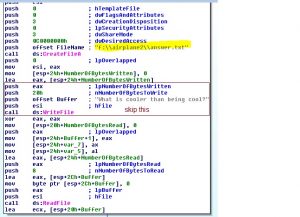
Now we can see the traffic, we can see a successful login and a file transfer.
We really want to see that is that file.
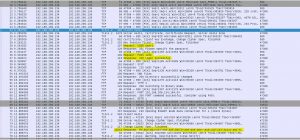
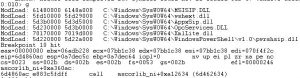
And again we see that magic number (50 4B 03 04) but this time it is xlsx and not zip.
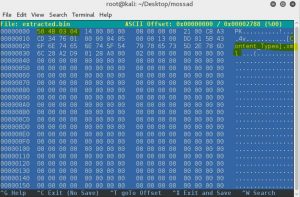
The xlsx contains random numbers, lets try using that ‘abcd’ file we got earlier and extract characters by given value as index.
And we are done!