This is a write-up of the CTF Shabak posted at April 2017.
Step 0
We begin with the following image:

And after we decode as base64 we get:
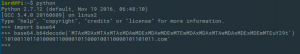
Browsing to the given address will lead us to the actual challenge, I honestly don’t know why all those challenges starting with base64.
We will choose the development team and will return back to research team once we are done.
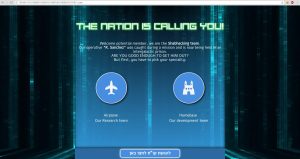
Homebase 1
“Staff Sergeant Foxy” Managed to get his hands on secret source code from the intergalactic prison!
unfortunately the code does not compile, Prove yourself worthy by compiling & executing the project.
We have unfinished project that we have to compile and run.
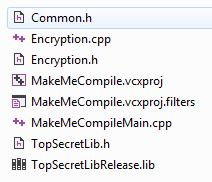
The mission isn’t that hard, we have some undeclared variables, useless code, incorrect function signatures.
After fixing all above and changing from debug to release, we get the flag!
Homebase 2
Success! Well.. Kinda…
Team Airplane managed to identify the encryption algorithm that the server uses to encrypt the content from the response.
Sadly, they only know how to write pseudo code, so as a programmer you need to buckle up buckaroo and implement the algorithm and decipher the response.
Now we to implement an algorithm and decipher the flag.
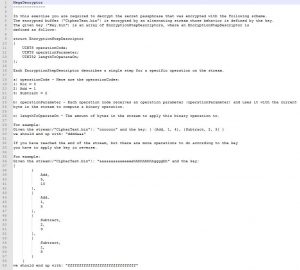
The algorithm is very straightforward and we also get an example to test our implementation.
Crafted python script:

The final result:
Homebase 3
Ok so our operative M. Smith managed to get to R. Sanchez’ cell in the prison, now he needs to transmit a message to him! Sadly the prison’s systems filter all messages that get through, so we need to figure out a way to fit its scheme.
You ‘member the decryption algorithm from the last mission? Yes you ‘member! now with a given encrypted message, you will need to find the correct key
Looks like we have to decrypt our way out through brute force:
![]()
We know that there are only 3 steps, and we know our alphabet.
By knowing the alphabet we can aim for a very specific range of values which will make brute force faster.
A-Z: 65-90 (decimal)
a-z: 97-122
Space, ‘.’, ‘?’: 32, 46, 63
First run of add,sub and xor yielded only one useful output:

Because add/sub will keep our values at the same range difference, we have to mix it up with xor in a way that all characters will be within a range of 26 (except for first capital letter and the last letter which reserved for space, ‘.’ and ‘?’).
At this point, after a quick google search, we found the desired quote (also the flag), which perfectly aligned with given encrypted message.
I consider this cheating because the key was never found, but hey – it works 🙂

