This is the second part of recent challenge posted by the Shabak.
Hey there fellow researcher! In every challenge in the ‘Airplane’ flow you’ll have to get to a point where a password is shown, feel free to use Dissasemblers, Debuggers or what ever you want.
Airplane 1
The intergalactic prison is in a secret location and we don’t know where it is…
We pulled some strings and found an intergalactic prison guard program which is willing to tell us the prison’s coordinates.
Sadly, we don’t know how to talk to it…
Show us what you got and get the prison’s location.
At this stage we have an executable file which should display the flag.
We can see an interesting path at the strings:
We created the file but Shabak will not make this challenge that easy, it is time to get our hands dirty and dive into assembly.
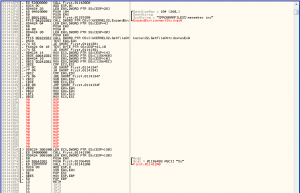
By searching for the folder, we can see that the program is reading folder’s attributes and compares them to hardcoded values.
There are two checks that will lead us to failure and will not let us reach the protected area which should reveal the flag.

Simply, fill these checks with NOPs and hope for the best.
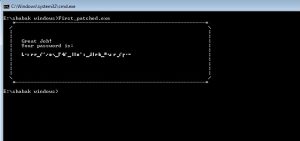
And as expected we have the flag!
Airplane 2
HOMEBASE team is working on deciphering the prison messaging system, luckily for us our operatives found a program that knows the encryption key, but unfortunately the program is refusing to talk (maybe a technological approach is better suited for this job since Spanish didn’t work).
We need you to*Make It Talk*
At this level we get a Portable Executable file – ‘Second.exe’.
We run it and he is asking for a password, after some random password is given he is trying to execute ‘GettingSchwifty.bat’ batch file.
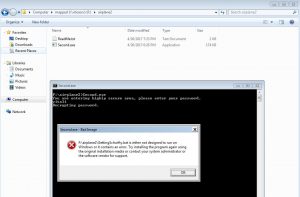
The file does not have any known magic number, and the content looks encrypted. I guess my password was wrong.
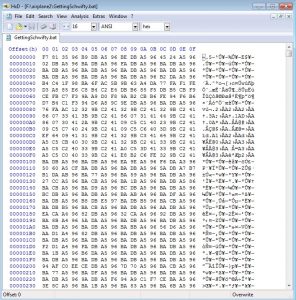
By looking at ‘Second.exe’ source code, we can see that ‘GettingSchwifty.bat’ is actually a DLL.
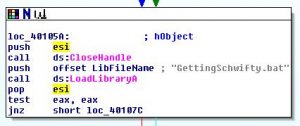
We also found out that XOR used to decrypt ‘GettingSchwifty.bat’ data.
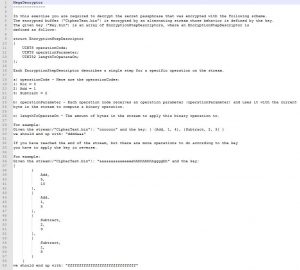
At this point we have two options, we can reverse ‘Second.exe’ to find what should be the password, or we can XOR ‘GettingSchwifty.bat’ with a key to get the correct data.
The second method is easier (at this case), we can do it because we know that the used algorithm was XOR on each 4 bytes, and we know what the output should be – a DLL.
DLLs have the same struct (same as PE) and by knowing this we can find what should be the key for ‘GettingSchwifty.bat’ and get our desired DLL.

(Image from adlice.com)
We will take the 32 bit starting from offset 0x20 (00 00 00 00 on ‘regular’ PE file), and compare them to the bits on ‘GettingSchwifty.bat’ (BA DB A5 96).
Because we know that XOR was used, [00000000 XOR 5ADBA596 = 5ADBA596] – and this is our key.
The following script did the trick:
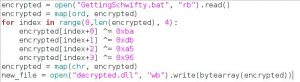
The next part is breaking that DLL, lets get to it.
We noticed the following code:
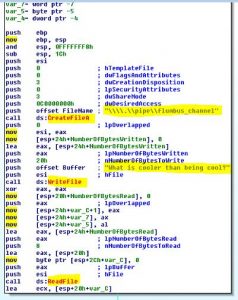
The DLL will open a pipe called ‘flumbus_channel’, ask us a question by writing it to the pipe, read our answer from the pipe.
The question is ‘What is cooler than being cool?‘.
I have never worked with pipes and I am too lazy to start coding, so I will just replace pipe’s path with my .txt file with the answer, so the DLL will read the answer straight from my file (also don’t forget to skip the WriteFile part so our answer will not get corrupted).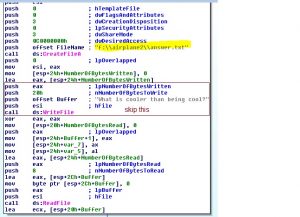
So after skipping the WriteFile part and reading the answer, the rest was clear and we have our password.